
IT Company cloud vulnerability management plays a crucial role in safeguarding an organization’s digital assets in the ever-evolving landscape of cloud computing. As businesses increasingly rely on cloud services for storing sensitive data and hosting critical applications, the potential for vulnerabilities rises significantly.
Implementing effective cloud vulnerability management not only helps in identifying and mitigating security risks but also ensures compliance with industry regulations and builds customer trust. This proactive approach is essential for protecting sensitive information from cyber threats and maintaining the integrity of business operations.
Table of Contents
ToggleWhat is Cloud Vulnerability Management for Businesses?
Cloud vulnerability management refers to the systematic process of identifying, assessing, and mitigating security vulnerabilities within cloud environments that businesses utilize. This involves using specialized tools and practices to detect weaknesses in cloud configurations, applications, and infrastructure that could be exploited by malicious actors.
Effective cloud vulnerability management not only enhances the security posture of an organization but also ensures compliance with industry standards and regulations. By prioritizing the identification and remediation of these vulnerabilities, businesses can safeguard sensitive data, maintain customer trust, and protect their reputation in an increasingly complex threat landscape.
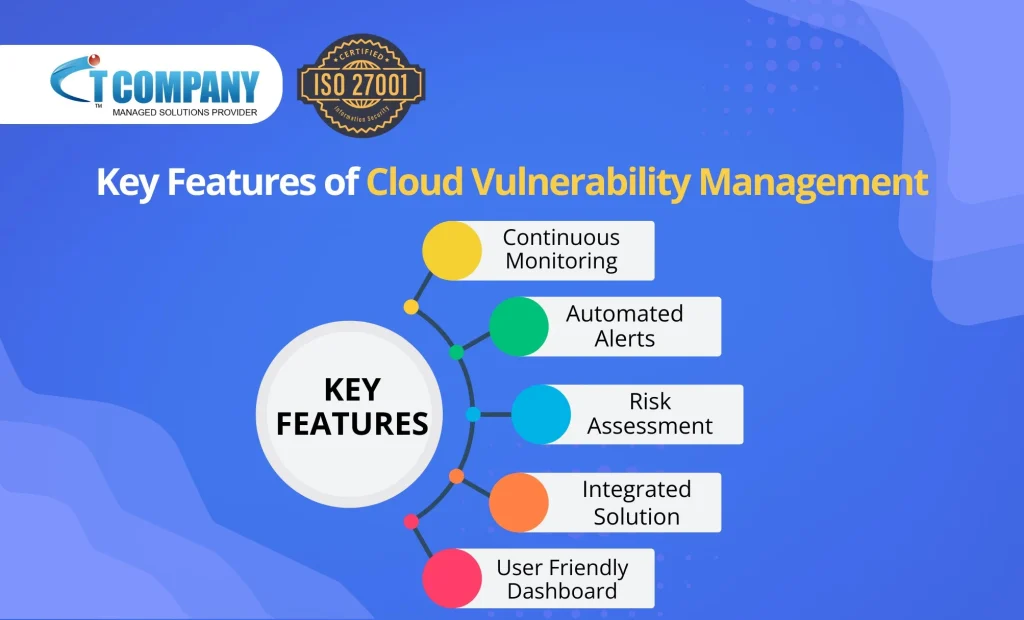
| Feature | Description |
| Continuous Monitoring | Ongoing scanning of cloud environments to detect vulnerabilities in real-time. |
| Automated Alerts | Instant notifications about potential security threats, enabling rapid response. |
| Risk Assessment | Evaluation of vulnerabilities based on their potential impact on business operations. |
| Integrated Solutions | Compatibility with existing security tools and workflows, streamlining vulnerability management. |
| Compliance Assistance | Tools and reporting to help meet industry standards and regulatory requirements. |
| User-Friendly Dashboard | Intuitive interface for easy tracking, reporting, and analysis of vulnerabilities. |
Key Challenges in Cloud Vulnerability Management
Managing cloud vulnerabilities presents several challenges that businesses must navigate to ensure a robust security posture. Here are the top five challenges, along with explanations and illustrations to enhance understanding:
Complexity of Cloud Environments
Modern cloud infrastructures often involve multiple services and layers, leading to increased complexity. As organizations adopt multi-cloud and hybrid environments, ensuring consistent security policies across different platforms can be daunting. For instance, consider a scenario where an organization uses both AWS and Azure; each platform has its own set of tools and configurations, making unified management challenging.
Dynamic Resource Allocation
The elastic nature of cloud resources means that instances can be spun up or down rapidly. This dynamic allocation can lead to security misconfigurations or unmonitored resources left vulnerable. Imagine a cloud instance that was provisioned for a short-term project but is left running unintentionally; this instance may not be adequately monitored, posing a risk.
Solutions Offered for Cloud Vulnerability Management
1. Adherence to Law
Ensure compliance with laws and regulations to mitigate legal risks and enhance security posture.
2. Invest in Training
Provide continuous training to staff, equipping them with the knowledge to identify and respond to security threats effectively.
3. Adopt a Risk-Based Approach
Focus on managing vulnerabilities by assessing risks and prioritizing actions based on potential impact.
4. Enhance Incident Response and Recovery Planning
Develop comprehensive plans to respond to incidents swiftly and recover operations with minimal downtime.
Partnering for Success
Our services cater to a broad spectrum of clients, including Cloud Service Providers, Enterprises, and SMEs. By understanding the unique challenges faced by each, we help tailor solutions that empower organizations to effectively manage cloud vulnerabilities.

Final Thoughts
In conclusion, managing cloud vulnerabilities involves recognizing the challenges, implementing strategic solutions, and cultivating a culture of continuous improvement. By partnering with us, businesses can bolster their defenses, ensuring resilience in today’s dynamic digital environment. Reach out to learn how our tailored solutions can advance your business’s cloud security to the next level.