
Maintaining your website’s security and integrity is critical. Despite our best efforts, unexpected events may develop, requiring the need for Website repair service. Whether it’s dealing with glitches, broken links, or security concerns, fast and effective maintenance is critical to maintaining a smooth online presence.
In this blog article, we’ll discuss the necessity of backing up your website before doing any website repair, as well as providing concrete strategies to keep your data secure during the process.
Table of Contents
ToggleWhy should you backup your website data before Performing Website Repair Procedures?
Your website data is made up of two primary parts: files and databases. Files contain code, photos, videos, plugins, themes, and other elements that contribute to the design and functioning of your website. Databases hold your material, such as posts, pages, comments, and settings, which you can control using a content management system (CMS), such as WordPress or Joomla. Hackers, viruses, and human error may all destroy, delete, or modify files and databases. Without a backup of your website data, you risk losing visitors, income, reputation, and rating.
How often should you backup your website’s content?

The frequency with which you backup your website is determined by how frequently you update it and how much data you are willing to lose. Ideally, you should backup your website data whenever you make a substantial update, such as adding new material, installing plugins, or upgrading your theme.
However, certain websites, particularly those with huge or sophisticated data collections, may find this impractical. A more reasonable strategy would be to backup your website data at least once a week, or more regularly if you have a high-traffic or dynamic site. You should also backup your website data before and after any important events, such as transferring to a new server, changing your domain name,
How can you manually back up your website data Before Performing Website Repair Procedures?
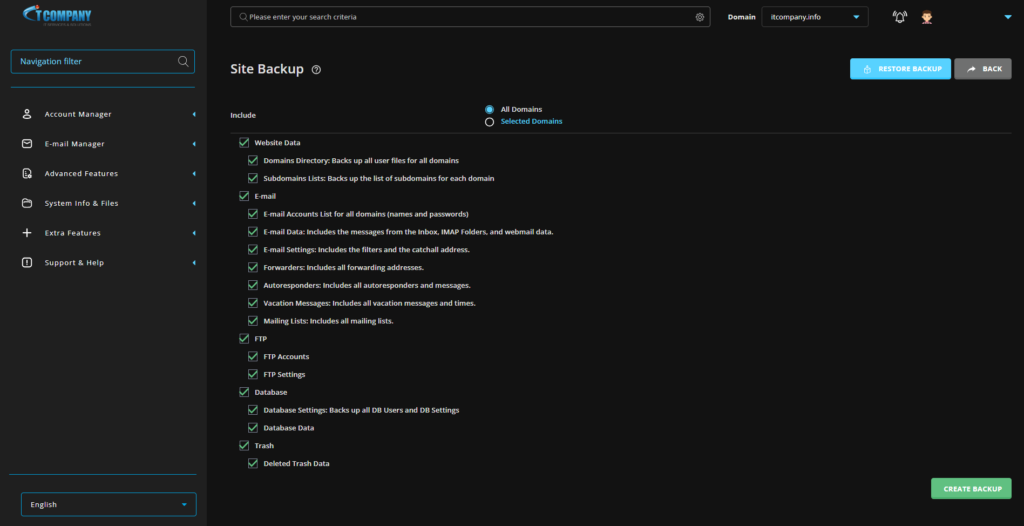
Manual backups of your website data may be done using your web hosting control panel and an FTP client. You may access and manage your website’s files and databases using your web hosting control panel. It allows you to export databases as SQL files and compress files.
Alternatively, you may connect to your web hosting services via an FTP program and move your files and directories there. This technique may take longer and require more bandwidth than utilizing your web hosting control panel.
How can you set up automatic backups Before Performing Website Repair Procedures?

Another option for backing up your website data is to utilize a Cloud based backup services, such as a plugin, script, or cloud provider. An automated backup tool or service may save you time and effort by producing and storing copies of your website data on a regular basis and in a specific place.
You may also use a script, such as rsync or cron, to copy your website’s files and databases to another server or location. Alternatively, you may utilize a cloud service such as Amazon S3 or Backblaze to have scalable and safe storage for your website backups.
How can I use a backup to recover the data on my website?
You must transfer your backup files and databases to your web hosting server in order to restore your website’s data from a backup. You may upload your backup files and folders to the relevant directories on your server using the FTP hosting or your web hosting control panel.
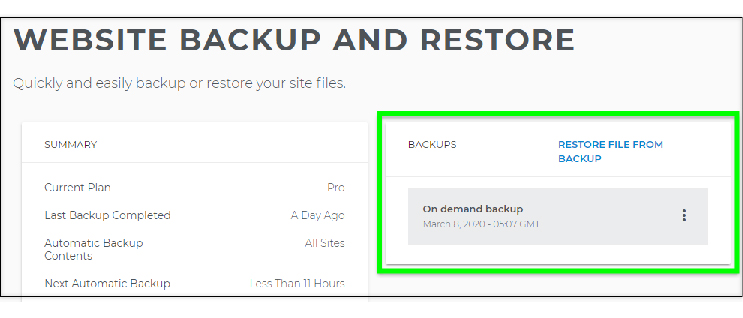
To import your backup databases onto your server, you may alternatively utilize a database administration tool or the control panel provided by your web provider. Make sure you have a current, legitimate backup that accurately reflects the current state and configuration of your website before attempting to restore its contents from a backup. Additionally, test your backup on a staging environment.
How do you validate the data on your website after a backup or restore?
Once you have backed up or restored your website’s data, you should confirm that both the website and its contents are operational and consistent. You may accomplish this by visiting your website and perusing through the various pages and posts to make sure the information and design load properly. To ensure that settings, plugins, themes, and other features are to your liking, log into the admin dashboard and evaluate them.
Conclusion
In conclusion, it is critical to guarantee the security and accuracy of the data on your website before doing any repairs. You may reduce the chances of data loss throughout the repair process and protect your important data by putting secure backup processes in place. IT Company’s Website repair service gives our customers piece of mind by prioritizing data safety in addition to fixing current problems. We prioritize the security and integrity of your priceless data, so you can trust us to effectively manage your website maintenance needs. For more information on how we can help you protect your online presence, get in touch with us right now.